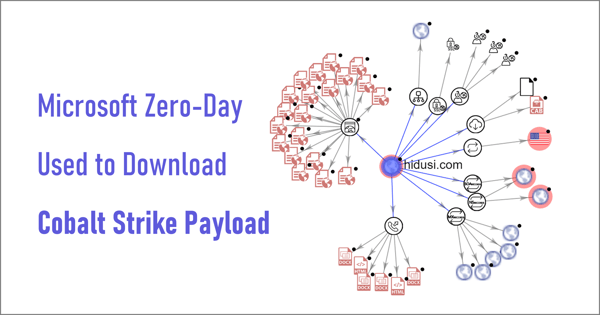
May 24, 2019 • John Bambenek
How to Mitigate Microsoft Windows Zero-Days Exploiting Enterprises & Giving Attackers Control
1Min read
•
critical vulnerability,
DNS Firewall,
microsoft,
Zero-day,
wannacry,
IP address,
dns security,
RDP