March 24, 2021 • Ofir Ashman
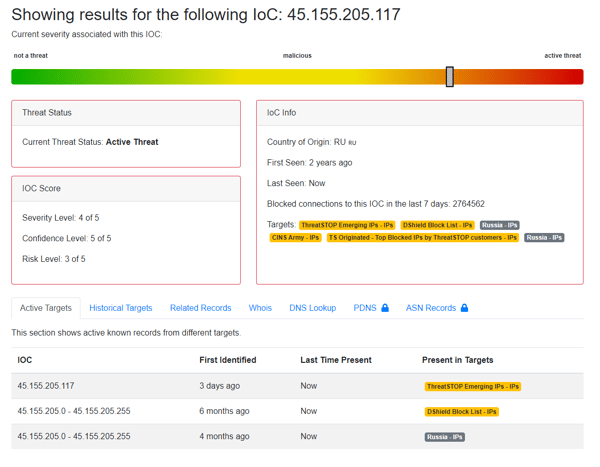
From Russia with Love: Selectel hosting some busy, malicious IP addresses
5Min read
•
check ip,
IP firewall,
targets,
Blocklists,
malicious IP,
threatstop-blocklists,
selectel

![More Love from Russia - More Bad IPs by Selectel like 45.146.164[.]38](https://www.threatstop.com/hs-fs/hubfs/ip_selectel.png?width=600&name=ip_selectel.png)
